Attacker Returns $153,000 Worth of Ether to Victim After Stealing $68 Million
Publikováno: 10.5.2024
An attacker involved in a $68 million address poisoning scam has returned $153,000 worth of Ether to the victim and expressed willingness to negotiate further.
The post Attacker Returns $153,000 Worth of Ether to Victim After Stealing $68 Million appeared first on Cryptonews.
An attacker involved in a $68 million address poisoning scam has exhibited a gesture of goodwill by returning $153,000 worth of Ether to the victim.
The address-poisoning attack initially saw the attacker tricking a user into transferring $68 million worth of Wrapped Bitcoin (WBTC), which has taken a new twist with the recent kind-hearted act of returning a fraction of the stolen funds.
Attacker Expressed Willingness To Negotiate
The attacker, operating under the alias “FakePhishing327990” on Etherscan, sent $153,000 Ether to the victim, accompanied by a message expressing willingness to negotiate and seeking communication via Telegram.
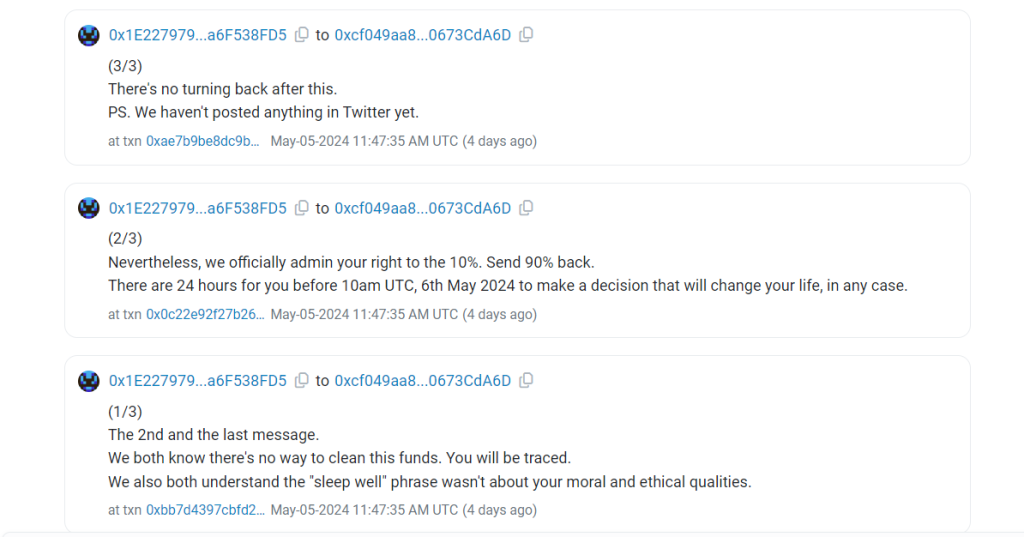
Blockchain data reveals that the victim, identified by their account ending in 8fD5, initiated communication with the attacker. The victim proposed a resolution in which the attacker would return 90% of the stolen funds in exchange for a 10% bounty and a commitment to refrain from legal action. The victim emphasized the inevitability of tracing the funds and provided a deadline for the decision.
Subsequently, another account controlled by the attacker, ending in 72F1, responded by sending 51 Ether to the victim. This symbolized a fraction of the stolen funds returned as a demonstration of goodwill. The accompanying message reiterated the attacker’s willingness to negotiate and requested the victim’s Telegram username for further communication.
The negotiation unfolds against the address poisoning scam, in which the attacker utilizes a smart contract to deceive the victim into transferring 1,155 WBTC by exploiting the appearance of similarity between addresses.
This sophisticated tactic, known as an “address poisoning attack,” involves spamming victims with transactions that mimic their own, ultimately leading to costly errors. Security experts caution users to scrutinize transaction details meticulously, particularly the sending address, to mitigate the risks associated with such attacks.
Phishing Attacks On Rise
An NFT trader recently fell victim to a phishing scam, losing over $145,000 worth of tokens. The trader, known as “tatis.eth,” was targeted by an attacker named “PinkDrainer,” who stole three valuable BAYC NFTs from the victim’s wallet.
BAYC, short for Bored Ape Yacht Club, is a collection of highly valued Ethereum-based NFTs featuring unique cartoon ape designs. The stolen NFTs were transferred to a phishing address and sold for 48.5 ETH.
This incident is part of a broader trend of phishing scams targeting cryptocurrency users, with notable losses reported in the first two months of 2024.
According to Scam Sniffer data, over $104 million worth of cryptocurrencies has been lost to phishing attacks in this period, with a significant portion coming from the Ethereum ecosystem.
The post Attacker Returns $153,000 Worth of Ether to Victim After Stealing $68 Million appeared first on Cryptonews.