Poly Network Defi Hacker Returns a Large Fraction of Tokens, Chainalysis Evaluates Hacker’s Onchain Movements
Publikováno: 12.8.2021
 On August 11, the blockchain intelligence firm Chainalysis published its findings on the recent Poly Network hack which saw the loss of approximately $611 million crypto tokens. The assessment from Chainalysis backed up the claims made by the security company called Slowmist that shows the hacker left a fingerprint on the relatively unknown exchange Hoo.com. […]
On August 11, the blockchain intelligence firm Chainalysis published its findings on the recent Poly Network hack which saw the loss of approximately $611 million crypto tokens. The assessment from Chainalysis backed up the claims made by the security company called Slowmist that shows the hacker left a fingerprint on the relatively unknown exchange Hoo.com. […]

On August 11, the blockchain intelligence firm Chainalysis published its findings on the recent Poly Network hack which saw the loss of approximately $611 million crypto tokens. The assessment from Chainalysis backed up the claims made by the security company called Slowmist that shows the hacker left a fingerprint on the relatively unknown exchange Hoo.com. As of August 11, at 4:18:39 p.m. (UTC), Poly Network details that the hacker has returned $260 million in assets so far.
Chainalysis Observes Hackers Onchain Fingerprints
The crypto community has been infatuated with the recent decentralized finance (defi) hack that exploited the Poly Network protocol. Bitcoin.com News reported on the aftermath of the hack and how the hacker started to troll the project with onchain messages.
On Wednesday, the blockchain surveillance firm Chainalysis published an in-depth report on what it discovered when it investigated the situation. According to Chainalysis, the hacker stole ETH, WETH, WBTC, UNI, RENBTC, USDT, USDC, DAI, SHIB, FEI, BNB, and various BEP-20 tokens.
In our most recent report, Bitcoin.com News discussed how the organization Slowmist claimed to have found some fingerprints left by the hacker. Chainalysis has confirmed some of the findings Slowmist disclosed prior to the hacker sending back roughly $4.7 million in assets.
Slowmist said that the hacker leveraged an exchange called Hoo.com and it was able to obtain an email address and associated IP address. Chainalysis explained why the hacker chose to leverage the relatively unknown crypto trading platform.
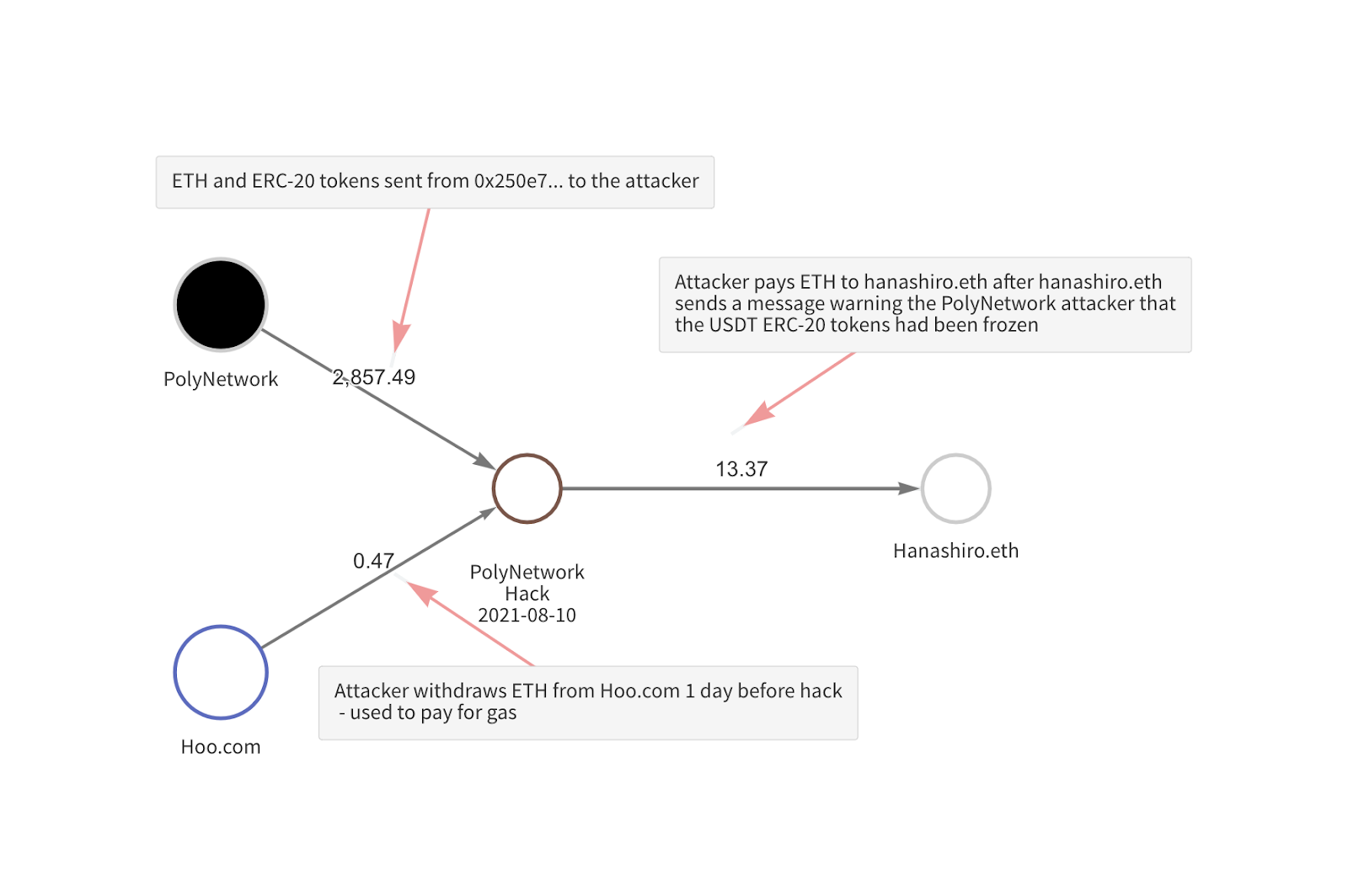
“We can see that the day before, the attacker withdrew 0.47 ETH from Hoo.com, which was used to pay for gas fees on transactions associated with the hack,” Chainalysis wrote. “Additionally, the attacker appears to have sent 13.37 ETH to a user known as Hanashiro.eth, who sent an ether transaction to the attacker with a message warning them that the USDT they’d stolen from Poly Network had been frozen.”
The blockchain surveillance firm also published a Chainalysis Reactor graph which shows how the hacker got started.
Hacker Compliments Poly Network and Says ‘Cross-Chain Hacking Is Hot’
Furthermore, the hacker has been communicating with the Poly Network team and an unknown white hat hacker. While returning fractions of the funds, the hacker has continuously said that the individual has “saved the project.”
There’s been a little Q&A as well and the hacker said that “cross-chain hacking is hot” and he or she was doing it “for fun.” The discussion highlights that when the hacker spotted the bug, they had “mixed feelings” about the situation. The hacker noted that he or she was “tired” during the conversation and even complimented the Poly Network at times calling it a “decent system.”
Toward the end of the Chainalysis report, it notes that the hacker has been communicating with the team and the company highlighted some of the token addresses that saw returns.
“It’s possible this is a ruse to make off with the unstolen USDT, but so far nothing suggests the attacker won’t continue to return the stolen funds,” Chainalysis detailed. The Poly Network team has been updating the community when coins have been returned via the project’s official Twitter account.
What do you think about the Poly Network defi hack that saw the theft of $600 million? Let us know what you think about this situation in the comments section below.