Seneca Hacker Returns $5.3M Amid Legal Threats, Keeps $1M Bounty
Publikováno: 29.2.2024
After exploiting the Seneca blockchain protocol, the hacker returned $5.3 million of the stolen funds to the project's Ethereum wallet, keeping a $1 million bounty for identifying a critical vulnerability.
The post Seneca Hacker Returns $5.3M Amid Legal Threats, Keeps $1M Bounty appeared first on Cryptonews.
After exploiting a vulnerability in the Seneca protocol on Wednesday, a hacker returned $5.3 million in stolen funds to the project on February 29.
The returned amount represents 80% of the reported $6.4 million stolen funds.
The hacker agreed to accept a 20% bounty, amounting to $1.28 million, as recognition for identifying the vulnerability within the smart contract.
Seneca Hacker Brings in 300 ETH
Blockchain security firm Peckshield reported on X (formerly Twitter) that the total Seneca funds returned is 1,537 ETH.
#PeckShieldAlert@SenecaUSD hacker-labeled address has returned 1,537 $ETH (worth ~$5.3m) to #Seneca: Deployer address & transferred 300 $ETH (~$1.04m) to 2 new addresses pic.twitter.com/hNOFMr1aTk
— PeckShieldAlert (@PeckShieldAlert) February 29, 2024
The hacker reportedly transferred 20% of the overall loot, amounting to 300 ETH, to two different crypto wallet addresses. This amount serves as the reward promised by the Seneca team for finding the bug in the project’s smart contract framework.
Dear Whitehat,
Please return the funds to the following Ethereum wallet address: 0xb7aF0Aa318706D94469d8d851015F9Aa12D9c53a
We are collaborating with third-party security providers and law enforcement to trace the funds and identify recipient wallets. Acting promptly is… pic.twitter.com/syIQQXHJSQ
— Seneca (@SenecaUSD) February 29, 2024
This development marks a significant step towards mitigating the impact of the exploit, with the Seneca team commending the collaboration with the hacker. The blockchain project lauded the Seneca funds returned through a white hat request as an “optimistic scenario” by the blockchain project.
The team provided further insights and revealed that the exploit targeted users’ wallets. Importantly, the hacker couldn’t access funds directly deposited into the project, which was its total value locked (TVL).
Despite Halborn Security’s audit of the Chamber Code smart contract prior to its deployment, a critical oversight was discovered within the segment of the code managing users’ wallets, which is why the exploit was not all-encompassing and only affected a section of its protocol.
We're happy to see 80% of funds have been returned.
Transaction link: https://t.co/VzqCvt24pF
The exploit involved assets held in users' wallets. The exploit didn't involve funds directly deposited into Seneca (Seneca's TVL).
The recovery of funds through a whitehat request…
— Seneca (@SenecaUSD) February 29, 2024
Additionally, the blockchain project stated that it is still gathering information on the exploit and will release a post-mortem update in the coming days.
Seneca Exploit, What Happened?
Seneca is a decentralized finance (DeFi) protocol that allows users to stake the native token $SEN to earn variable amounts of yields on them.
PeckShield Inc. first captured the attack, revealing a critical approval bug in the Seneca protocol.
Hi @SenecaUSD We have confirmed the critical approval bug in Seneca protocol that allows to steal funds from approving users.
Please revoke your approvals from the following addresses:
– eth: 0xbc83f2711d0749d7454e4a9d53d8594df0377c05
-arb:… https://t.co/bIG72A65Wlpic.twitter.com/cuOf9gobga— PeckShield Inc. (@peckshield) February 28, 2024
It also noted that this approval bug would allow hackers to steal users’ funds as the smart contract was not ‘pausable’ even though the capacity was there.
Seneca revoked the highlighted addresses and informed the hacker that it was working with security operatives and law enforcement agents to track down the stolen funds.
Dear Whitehat,
Please return the funds to the following Ethereum wallet address: 0xb7aF0Aa318706D94469d8d851015F9Aa12D9c53a
We are collaborating with third-party security providers and law enforcement to trace the funds and identify recipient wallets. Acting promptly is… pic.twitter.com/syIQQXHJSQ
— Seneca (@SenecaUSD) February 29, 2024
Crypto losses have become a normal staple in the industry, however. PeckShield Alert’s report recorded over 600 major malicious attacks in 2023, resulting in roughly $2.61 billion in losses. Only $674.9 million out of the losses were recovered.
#PeckShieldAlert 2023 saw 600+ major hacks in the crypto space, resulting in ~$2.61B in losses, with $674.9M recovered.
$1.51B lost to hacks (excluding #Multichain unauthorized withdrawals) & $1.1B to scams. This marks a 27.78% decrease from 2022. #DeFi protocols remained prime… pic.twitter.com/G7PIU3WyrX— PeckShieldAlert (@PeckShieldAlert) January 29, 2024
Hacks accounted for $1.51 billion in losses, excluding the Multichain network unauthorized withdrawals of roughly $200 million. Crypto scams resulted in a loss of $1.1 billion.
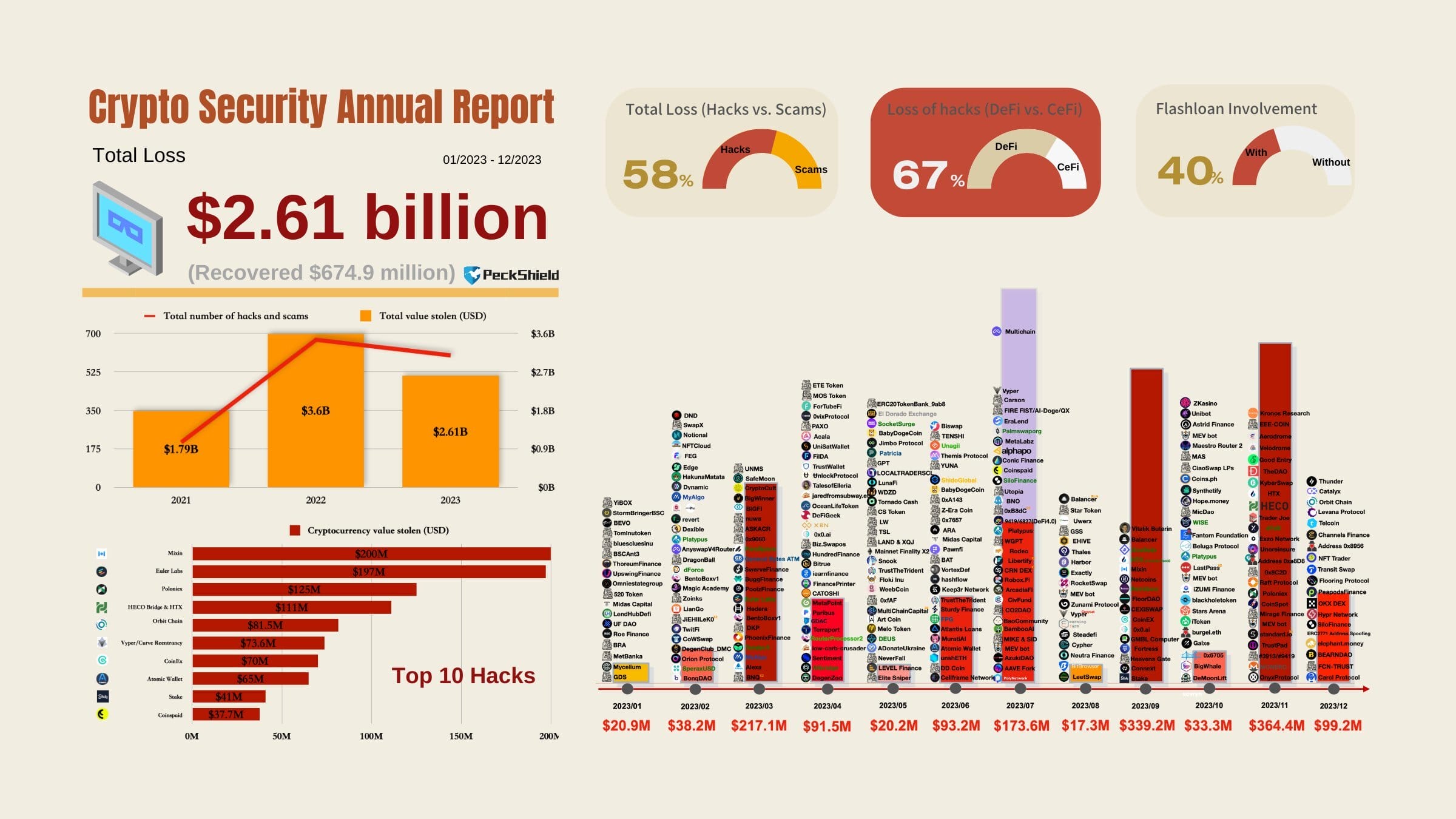
The total losses recorded marked a 27.78% decrease from that of 2022. Meanwhile, DeFi-facing protocols were the principal targets of crypto hacks and scams, with 67% of total losses coming from that ecosystem.
The post Seneca Hacker Returns $5.3M Amid Legal Threats, Keeps $1M Bounty appeared first on Cryptonews.